Show a real disk opened up and illustrate the components
Devices are often quite complicated to manage and a separate computer, called a controller, is used to translate simple commands (read sector 123456) into what the device requires (read cylinder 321, head 6, sector 765). Actually the controller does considerably more, e.g. calculates a checksum for error detection.
How does the OS know when the I/O is complete?

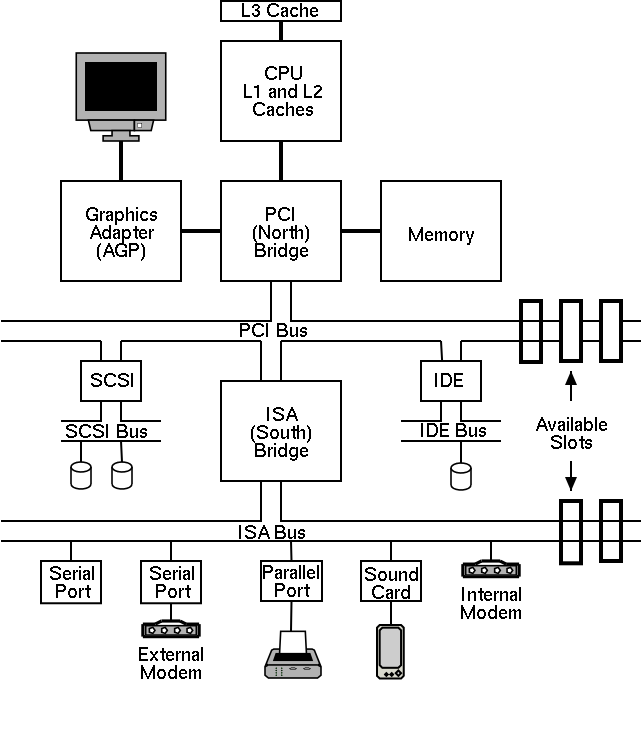
I don't care so much about the names of the buses, but the diagram
given in the book doesn't show a modern design. The one on the right
does.
This will be very brief. Much of the rest of the course will consist in ``filling in the details''.
A program in execution. If you run the same program twice, you have created two processes. For example if you have two editors running in two windows, each instance of the editor is a separate process.
Often one distinguishes the state or context (memory image, open files) from the thread of control. Then if one has many threads running in the same task, the result is a ``multithreaded processes''.
The OS keeps information about all processes in the process table. Indeed, the OS views the process as the entry. This is an example of an active entity being viewed as a data structure (cf. discrete event simulations). An observation made by Finkel in his (out of print) OS textbook.
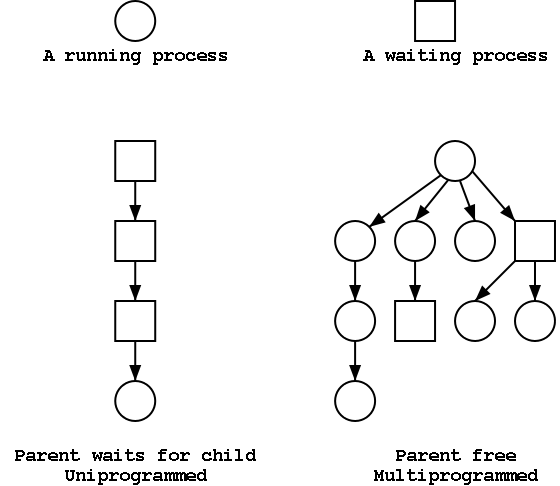
The set of processes forms a tree via the fork system call. The forker is the parent of the forkee, which is called a child. If the system blocks the parent until the child finishes, the ``tree'' is quite simple, just a line. But the parent (in many OSes) is free to continue executing and in particular is free to fork again producing another child.
A process can send a signal to another process to cause the latter to execute a predefined function (the signal handler). This can be tricky to program since the programmer does not know when in his ``main'' program the signal handler will be invoked.
Each user is assigned User IDentification (UID) and all processes created by that user have this UID. One UID is special (the superuser or administratore) and has extra privileges. A child has the same UID as its parent. It is sometimes possible to change the UID of a running process. A group of users can be formed and given a Group IDentification, GID.
Access to files and devices can be limited to a given UID or GID.
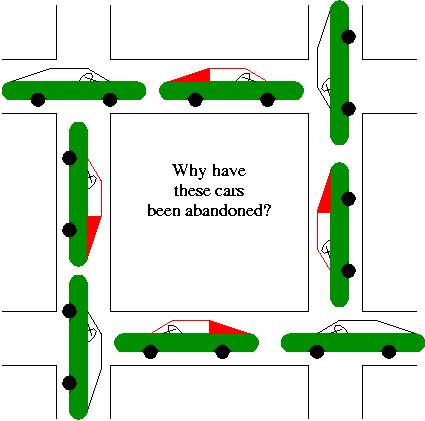
A set of processes each of which is blocked by a process in the
set. The automotive equivalent, shown at right, is gridlock.
Each process requires memory. The loader produces a load module that assumes the process is loaded at location 0. The operating system ensures that the processes are actually given disjoint memory. Current operating systems permit each process to be given more (virtual) memory than the total amount of (real) memory on the machine.
There are a wide variety of I/O devices that the OS must manage. For example, if two processes are printing at the same time, the OS must not interleave the output. The OS contains device specific code (drivers) for each device as well as device-independent I/O code.
Modern systems have a hierarchy of files. A file system tree.
You can name a file via an absolute path starting at the root directory or via a relative path starting at the current working directory.
In addition to regular files and directories, Unix also uses the file system namespace for devices (called special files, which are typically found in the /dev directory. Often utilities that are normally applied to (ordinary) files can be applied as well to some special files. For example, when you are accessing a unix system using a mouse and do not have anything serious going on (e.g., right after you log in), type the following command
cat /dev/mouse
and then move the mouse. You kill the cat by typing cntl-C. I tried
this on my linux box and no damage occurred. Your mileage may vary.
Before a file can be accessed, it must be opened and a file descriptor obtained. Many systems have standard files that are automatically made available to a process upon startup. These (initial) file descriptors are fixed
A convenience offered by some command interpretors is a pipe or pipeline. The pipeline
dir | wcwhich pipes the output dir into a character/word/line counter, will give the number of files in the directory (plus other info).
Files and directories normally have permissions
The command line interface to the operating system. The shell permits the user to
Homework: 8