Operating Systems
2000-01 Fall
M 5:00-6:50
Ciww 109
Allan Gottlieb
gottlieb@nyu.edu
http://allan.ultra.nyu.edu/~gottlieb
715 Broadway, Room 1001
212-998-3344
609-951-2707
email is best
================ Start Lecture #14
================
Remark:
We are doing 6.6 before 6.5 since 6.6 is easier.
6.6: Deadlock Prevention
Attack one of the coffman/havender conditions
6.6.1: Attacking Mutual Exclusion
Idea is to use spooling instead of mutual exclusion. Not
possible for many kinds of resources
6.6.2: Attacking Hold and Wait
Require each processes to request all resources at the beginning
of the run. This is often called One Shot.
6.6.3: Attacking No Preempt
Normally not possible.
6.6.4: Attacking Circular Wait
Establish a fixed ordering of the resources and require that they
be requested in this order. So if a process holds resources #34 and
#54, it can request only resources #55 and higher.
It is easy to see that a cycle is no longer possible.
6.5: Deadlock Avoidance
Let's see if we can tiptoe through the tulips and avoid deadlock
states even though our system does permit all four of the necessary
conditions for deadlock.
An optimistic resource manager is one that grants every
request as soon as it can. To avoid deadlocks with all four
conditions present, the manager must be smart not optimistic.
6.5.1 Resource Trajectories
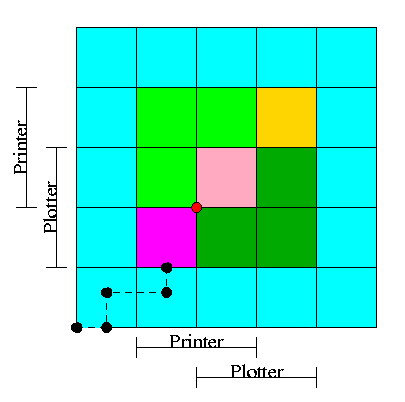
- We have two processes H (horizontal) and V.
- The origin represents them both starting.
- Their combined state is a point on the graph.
- The parts where the printer and plotter are needed by each process
are indicated.
- The dark green is where both processes have the plotter and hence
execution cannot reach this point.
- Light green represents both having the printer; also impossible.
- Pink is both having both printer and plotter; impossible.
- Gold is possible (H has plotter, V has printer), but you can't get
there.
- The upper right corner is the goal both processes finished.
- The red dot is ... (cymbals) deadlock. We don't want to go there.
- The cyan is safe. From anywhere in the cyan we have horizontal
and vertical moves to the finish line without hitting any impossible
area.
- The magenta interior is very interesting. It is
- Possible: each processor has a different resource
- Not deadlocked: each processor can move within the magenta
- Deadly: deadlock is unavoidable. You will hit a magenta-green
boundary and then will no choice but to turn and go to the red dot.
- The cyan-magenta border is the danger zone
- The dashed line represents a possible execution pattern.
- With a uniprocessor no diagonals are possible. We either move to
the right meaning H is executing or move up indicating V.
- The trajectory shown represents.
- H excuting a little.
- V excuting a little.
- H executes; requests the printer; gets it; executes some more.
- V executes; requests the plotter.
- The crisis is at hand!
- If the resource manager gives V the plotter, the magenta has been
entered and all is lost. ``Abandon all hope yee who enter here''
--Dante.
- The right thing to do is to deny the request, let H execute moving
horizontally under the magenta and dark green. At the end of the dark
green, no danger remains, both processes will complete successfully.
Victory!
- This procedure is not practical for a general purpose OS since it
requires knowing the programs in advance. That is, the resource
manager, knows in advance what requests each process will make and in
what order.
6.5.2: Safe States
Avoiding deadlocks given some extra knowledge.
- Not surprisingly, the resource manager knows how many units of each
resource it had to begin with.
- Also it knows how many units of each resource it has given to
each process.
- It would be great to see all the programs in advance and thus know
all future requests, but that is asking for too much.
- Instead, each process when it starts gives its maximum usage.
That is each process at startup states, for each resource, the maximum
number of units it can possibly ask for. This is called the
claim of the process.
- If during the run the process asks for more than its claim,
abort it.
- If it claims more than it needs, the result is that the
resource manager will be more conservative than need be and there
will be more waiting.
Definition: A state is safe
if there one can find an ordering of the processes such that if the
processes are run in this order, they will all terminate (assuming
none exceeds its claim).
Give an example of all four possibilities. A state that is
- Safe and deadlocked
- Safe and not deadlocked
- Not safe and deadlocked
- Not safe and not deadlocked
A manager can determine if a state is safe.
- Since the manager know all the claims, it can determine the maximum
amount of additional resources each process can request.
- The manager knows how many units of each resource it has left.
The manager then follows the following procedure, which is part of
Banker's Algorithms discovered by Dijkstra, to
determine if the state is safe.
- If there are no processes remaining, the state is
safe.
- Seek a process P whose max additional requests is less than
what remains (for each resource).
- If no such process can be found, then the state is
not safe.
- The banker (manager) knows that if it refuses all requests
excepts those from P, then it will be able to satisfy all
of P's requests. Why?
Look at how P was chosen.
- The banker now pretends that P has terminated (since the banker
knows that it can guarantee this will happen). Hence the banker
pretends that all of P's currently held resources are returned. This
makes the banker richer and hence perhaps a process that was not
eligible to be chosen as P previously, can now be chosen.
- Repeat these steps.
Example 1
| process | claim | current |
|---|
| X | 3 | 1 |
| Y | 11 | 5 |
| Z | 19 | 10 |
| total | | 16 |
- One resource type R with 22 unit
- Three processes X, Y, and Z with claims 3, 11, and 19 respectively.
- Currently the processes have 1, 5, and 10 units respectively.
- Hence the manager currently has 6 units left.
- Also note that the max additional needs for processes are 2, 6, 9
- So the manager cannot assure (with its current
remaining supply of 6 units that Z can terminate. But that is
not the question.
- This state is safe
- Use 2 units to satisfy X; now the manager has 7 units.
- Use 6 units to satisfy Y; now the manager has 12 units.
- Use 9 units to satisfy Z; done!
Example 2
| process | claim | current |
|---|
| X | 3 | 1 |
| Y | 11 | 5 |
| Z | 19 | 12 |
| total | | 18 |
Assume that Z now requests 2 units and we grant them.
- Currently the processes have 1, 5, and 12 units respectively.
- The manager has 4 units.
- The max additional needs are 2, 6, and 7.
- This state is unsafe
- Use 2 unit to satisfy X; now the manager has 5 units.
- Y needs 6 and Z needs 7 so we can't guarantee satisfying either
- Note that we were able to find a process that can terminate (X)
but then we were stuck. So it is not enough to find one process.
Must find a sequence of all the processes.
Remark: An unsafe state is not necessarily
a deadlocked state. Indeed, if one gets lucky all processes may
terminate successfully. A safe state means that the manager can
guarantee that no deadlock will occur.
6.5.3: The Banker's Algorithm (Dijkstra) for a Single Resource
The algorithm is simple: Stay in safe states.
- Check before any process starts that the state is safe (this means
that no process claims more than the manager has). If not, then this
process is trying to claim more than the system has so cannot be run.
- When the manager receives a request, it pretends to grant it and
checks if the resulting state is safe. If it is safe the request is
granted, if not the process is blocked.
- When a resource is returned, the manager checks to see if any of
the pending requests can be granted (i.e., if the result would now be
safe). If so the request is granted and the manager checks to see if
another can be granted.
6.5.4: The Banker's Algorithm for Multiple Resources
At a high level the algorithm is identical: Stay in safe states.
- What is a safe state?
- The same definition (if processes are run in a certain order they
will all terminate).
- Checking for safety is the same idea as above. The difference is
that to tell if there enough free resources for a processes to
terminate, the manager must check that for all
resources, the number of free units is at least equal to the max
additional need of the process.
Limitations of the banker's algorithm
- Often users don't know the maximum requests a process will make.
They can estimate conservatively (i.e., use big numbers for the claim)
but then the manager becomes very conservative.
- New processes arriving cause a problem (but not so bad as
Tanenbaum suggests).
- The process's claim must be less than the total number of
units of the resource in the system. If not, the process is not
accepted by the manager.
- Since the state without the new process is safe, so is the
state with the new process! Just use the order you had originally
and put the new process at the end.
- Insuring fairness (starvation freedom) needs a little more
work, but isn't too hard either (once an hour stop taking new
processes until all current processes finish).
- A resource becoming unavailable (e.g., a tape drive breaking), can
result in an unsafe state.
Homework: 11, 14 (do not hand in).
6.7: Other Issues
6.7.1: Two-phase locking
This is covered (MUCH better) in a database text. We will skip it.
6.7.2: Non-resource deadlocks
You can get deadlock from semaphores as well as resources. This is
trivial. Semaphores can be considered resources. P(S) is request S
and V(S) is release S. The manager is the module implementing P and
V. When the manager returns from P(S), it has granted the resource S.
6.7.3: Starvation
As usual FCFS is a good cure. Often this is done by priority aging
and picking the highest priority process to get the resource. Also
can periodically stop accepting new processes until all old ones
get their resources.
The End: Good luck on the final

