Operating Systems
2000-01 Fall
M 5:00-6:50
Ciww 109
Allan Gottlieb
gottlieb@nyu.edu
http://allan.ultra.nyu.edu/~gottlieb
715 Broadway, Room 1001
212-998-3344
609-951-2707
email is best
================ Start Lecture #11
================
Note:
There was a typo or two in the symlinking directories section (picture
should show /B not /B/new, and cd -P goes to / not /B). The giant
page and the lecture-10 page have been fixed.
- Privacy
- An enormously serious (societal) subject.
4.4.2: Famous flaws
- Good bathroom reading.
- Trojan horse attack: Planing a program of your choosing in place
of a well known program and having an unsuspecting user execute it.
- Some trivial examples:
- Install a new version of login that does everything normal,
but then mails the username and plaintext password to
gottlieb@nyu.edu.
- Put a new version of ls in your home directory and ask the
sysadmin for help. ``Hopefully he types ls while in your
directory and has . early in his path''.
4.4.3: The internet worm
- A worm divides itself and sends one portion to another machine.
- Different from a virus (see below).
- The famous internet (Morris) worm exploited silly bugs in unix to
crack systems automatically.
- Specifically, it exploited careless use of gets(), which does not
check the length of its argument.
- Attacked Sun and Vax unix systems.
- NYU was hit hard; but not our lab, which had IBM RTs.
4.4.4: Generic Security attacks
More bathroom reading
Viruses
- A virus attaches itself to (``infects'') a part of the system so
that it remains until explicitly removed. In particular, rebooting
the system does not remove it.
- Attach to an existing program or to a portion of the disk that is
used for booting.
- When the virus is run it tries to attach itself to other files.
- Often implemented the same was as a binary patch: Change the first
instruction to jump to somewhere where you put the original first
instruction, then your patch, then a jump back to the second
instruction.
4.4.5: Design principles for security
More bathroom reading
4.4.6: User authentication
Passwords
- Software to crack passwords is publically available.
- Use this software for prevention.
- One way to prevent cracking passwords is to use instead one time
passwords: e.g. SecurId.
- Current practice here and elsewhere is that when you telnet to a
remote machine, your password is sent in the clear along the ethernet.
So maybe .rhosts aren't that bad after all.
Physical identification
Opens up a bunch of privacy questions. For example,
should we require fingerprinting for entering the subway?
Homework: 15, 16, 19, 24.
4.5: Protection mechanisms
4.5.1: Protection domains
- We distinguish between Objects, which are
passive, and subjects, which are active.
- For example, processes (subjects) examine files (objects).
- Protection domain: A collection of (object,
rights) pairs.
- At any given time a subject is given a protection domain that
specifies its rights.
- In Unix a subject's domain is determined by its (uid, gid) (and
whether it is in kernel mode).
- Generates a matrix called the protection or permission matrix.
- Each row corresponds to a domain (i.e. a subject at some time).
- Each column corresponds to an object (e.g., a file or device).
- Each entry gives the rights the domain/subject has on this object.
- Can model Unix suid/sgid by permitting columns whose headings are
domains and the only right possible in the corresponding entries is
entry. If this right is present, the subject corresponding to the row
can s[ug]id to the new domain, which corresponds to the column.
4.5.2: Access Control Lists (ACLs)
Keep the columns of the matrix separate and drop the null entries.
4.5.3: Capabilities
Keep the rows of the matrix separate and drop the null entries.
4.5.4: Protection models
Give objects and subjects security levels and enforce:
- A subject may read only those objects whose level is at or below
her own.
- A subject may write only those objects whose level is at or
above her own.
4.5.5: Covert channels
The bad guys are getting smart and use other means of getting out
information. For example give good service for a zero and bad for a
one. The figure of merit is the rate at which bits can be sent,
i.e. the bandwidth of the covert channel.
Homework: 20.
Chapter 5: Input/Output
5.1: Principles of I/O Hardware
5.1.1: I/O Devices
- Not much to say. Devices are varied.
- Block versus character devices:
- Devices, such as disks and CDROMs, with addressable chunks
(sectors in this case) are called block
devices,
These devices support seeking.
- Devices, such as Ethernet and modem connections, that are a
stream of characters are called character
devices.
These devices do not support seeking.
- Some cases, like tapes, are not so clear.
5.1.2: Device Controllers
These are the ``real devices'' as far as the OS is concerned. That
is the OS code is written with the controller spec in hand not with
the device spec.
The figure in the book is so oversimplified as to be borderline
false. The following picture is closer to the truth (but really there
are several I/O buses of different speeds).
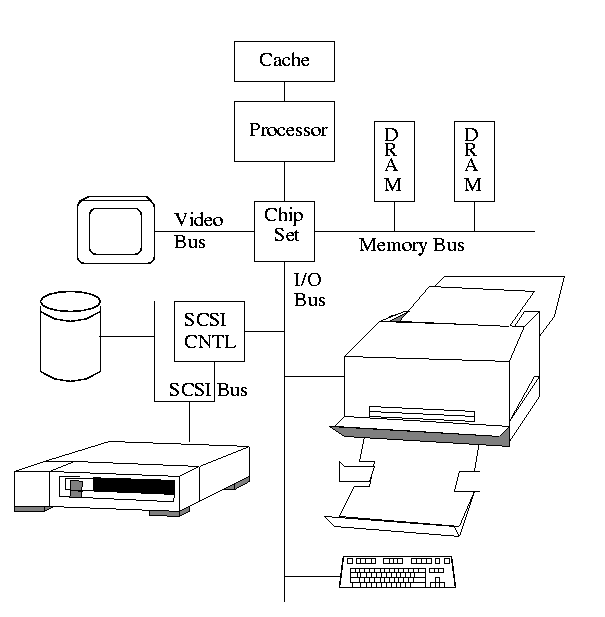
- The controller abstracts away some of the low level features of
the device.
- For disks, the controller does error checking, buffering and
handles interleaving of sectors. (Sectors are interleaved if the
controller or CPU cannot handle the data rate and would otherwise have
to wait a full revolution. This is not a concern with modern systems
since the electronics have increased in speed faster than the
devices.)
- For analog monitors (CRTs) the controller does
a great deal. Analog video is far from a bunch of ones and
zeros.
- Controllers are also called adaptors.
Using a controller
Think of a disk controller and a read request. The goal is to copy
data from the disk to some portion of the central memory. How do we
do this?
- The controller contains a microprocessor and memory and is
connected to the disk (by a cable).
- When the controller asks the disk to read a sector, the contents
come to the controller via the cable and are stored by the controller
in its memory.
- The question is how does the OS, which is running on another
processor, let the controller know that a disk read is desired and how
is the data eventually moved from the controllers memory to the
general system memory.
- Typically the interface the OS sees consists of some device
registers located on the controller.
- These are memory locations into which the OS writes
information such as sector to access, read vs. write, length,
where in system memory to put the data (for a read) or from where
to take the data (for a write).
- There is also typically a device register that acts as a
``go button''.
- There are also devices registers that the OS reads, such as
status of the controller, errors found, etc.
- So now the question is how does the OS read and write the device
register.
- With Memory-mapped I/O the device registers
appear as normal memory. All that is needed is to know at which
address each device regester appears. Then the OS uses normal
load and store instructions to write the registers.
- Some systems instead have a special ``I/O space'' into which
the registers are mapped and require the use of special I/O
instructions to accomplish the load and store. From a conceptual
point of view there is no difference between the two models.
Homework: 2
5.1.3: Direct Memory Access (DMA)
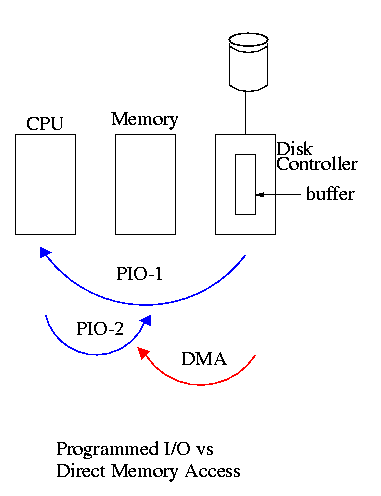
- With or without DMA, the disk controller pulls the desired data
from the disk to its buffer (and pushes data from the buffer to the
disk).
- Without DMA, i.e., with programmed I/O (PIO), the
cpu then does loads and stores (or I/O instructions) to copy the data
from the buffer to the desired memory location.
- With a DMA controller, the controller writes the memory without
intervention of the CPU.
- Clearly DMA saves CPU work. But this might not be important if
the CPU is limited by the memory or by system buses.
- Very important is that there is less data movement so the buses
are used less and the entire operation takes less time.
- Since PIO is pure software it is easier to change, which is an
advantage.
- DMA does need a number of bus transfers from the CPU to the
controller to specify the DMA. So DMA is most effective for large
transfers where the setup is amortized.
- Why have the buffer? Why not just go from the disk straight to
the memory.
Answer: Speed matching. The disk supplies data at a fixed rate, which might
exceed the rate the memory can accept it. In particular the memory
might be busy servicing a request from the processor or from another
DMA controller.
Homework: 5


